
In an era where data is the most valuable currency in research, the perimeter of cybersecurity has moved from the office desk to the laboratory bench.
As lab equipment becomes increasingly networked and integrated into cloud ecosystems, standard password protection is no longer sufficient to safeguard intellectual property or ensure experimental integrity.
Implementing Multi-Factor Authentication (MFA) for lab hardware represents a critical shift toward a Zero Trust environment, where every access point is verified.
By layering security protocols, labs can prevent unauthorized usage, mitigate the risk of data breaches, and maintain the rigorous standards required by modern scientific discovery.
Standard laboratories often house equipment worth millions of dollars, frequently containing sensitive proprietary data. Simple passwords are easy to crack, share, or lose.

MFA adds a layer of something you have or something you are to the traditional something you know.
Many labs must adhere to strict guidelines such as 21 CFR Part 11 (FDA), HIPAA, or ISO 27001. These standards often require robust access controls and traceable user activity, which MFA provides out of the box.

By requiring a secondary check, MFA ensures that only trained staff who possess the necessary credentials (like a physical key or biometric scan) can operate dangerous or highly sensitive machinery.

With the rise of Smart Labs, researchers often monitor experiments remotely. MFA is the gold standard for securing these remote connections against external hacking attempts.

Not every piece of equipment requires high-level MFA.
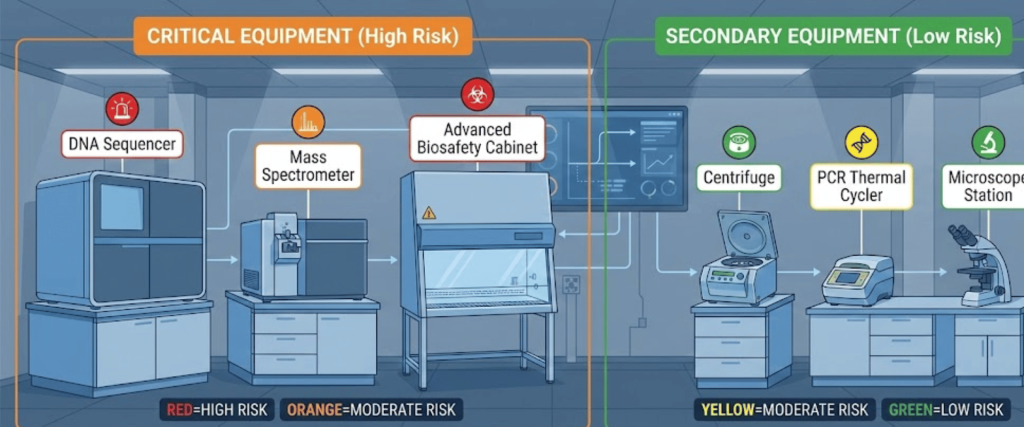
In a lab environment, the choice of MFA must not hinder productivity.

For a seamless workflow, the MFA protocol should be integrated into your LIMS or Electronic Lab Notebook (ELN).
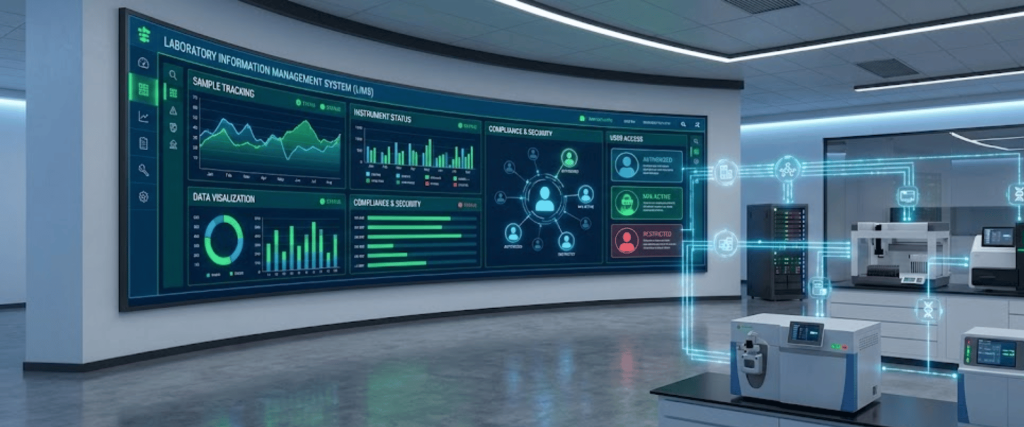
This creates a centralized hub where permissions can be revoked or granted instantly across all connected hardware.
Adopting Multi-Factor Authentication for lab equipment is a vital investment in the security and credibility of your research environment.
By layering verification methods, you effectively shield sensitive data from breaches while ensuring that only qualified personnel handle critical machinery.
This transition not only satisfies modern regulatory demands but also future-proofs your facility against the growing landscape of digital and physical threats.
Protecting your lab’s integrity today ensures that the scientific breakthroughs of tomorrow remain secure and undisputed.
While adding a security step takes a few extra seconds, low-friction methods like NFC badge tapping or biometric scans are designed to be nearly instantaneous. When integrated correctly, the minor increase in time is vastly outweighed by the reduction in risk and the automation of access logs, which actually saves time during administrative audits.
For older, offline machinery, you can use hardware-based solutions such as smart-plug interlocks or physical cabinet locks that require an MFA-authorized key to power on the device. Alternatively, a dedicated Gateway PCcan be used as a terminal that requires MFA before it sends a signal to unlock the equipment’s software interface.
In environments where gloves or masks are mandatory, biometric methods like fingerprint or facial recognition may be impractical. In these cases, NFC (Near Field Communication) badges, or RFID fobs, are the best choice. They allow researchers to authenticate by simply tapping their badge against a sensor, which works perfectly even through protective clothing.
Since 1992, Applied Physics Corporation has been a leading global provider of precision contamination control and metrology standards. We specialize in airflow visualization, particle size standards, and cleanroom decontamination solutions for critical environments.